Protect your infrastructure with LECS, the first Plug & Play cybersecurity device that protects any LAN, Cloud infrastructure and industrial facilities from the most dangerous cyber attacks and threats.


LECS has a zero knowledge architecture and is maintenance-free. Connected to the network switch, the LECS computer security device analyses traffic, movements inside and outside the network and once an anomaly is detected, it classifies it and acts according to the degree of severity with a modulated response to the attack.
The artificial intelligence algorithms that work synergistically and in parallel to protect an entire network segment are:
Performing detection and classification of anomalies on network traffic, acting with countermeasures and targeted responses in cases of critical threats, and performing intelligent forecasting that provides update feedback based on the latest detected statistics.
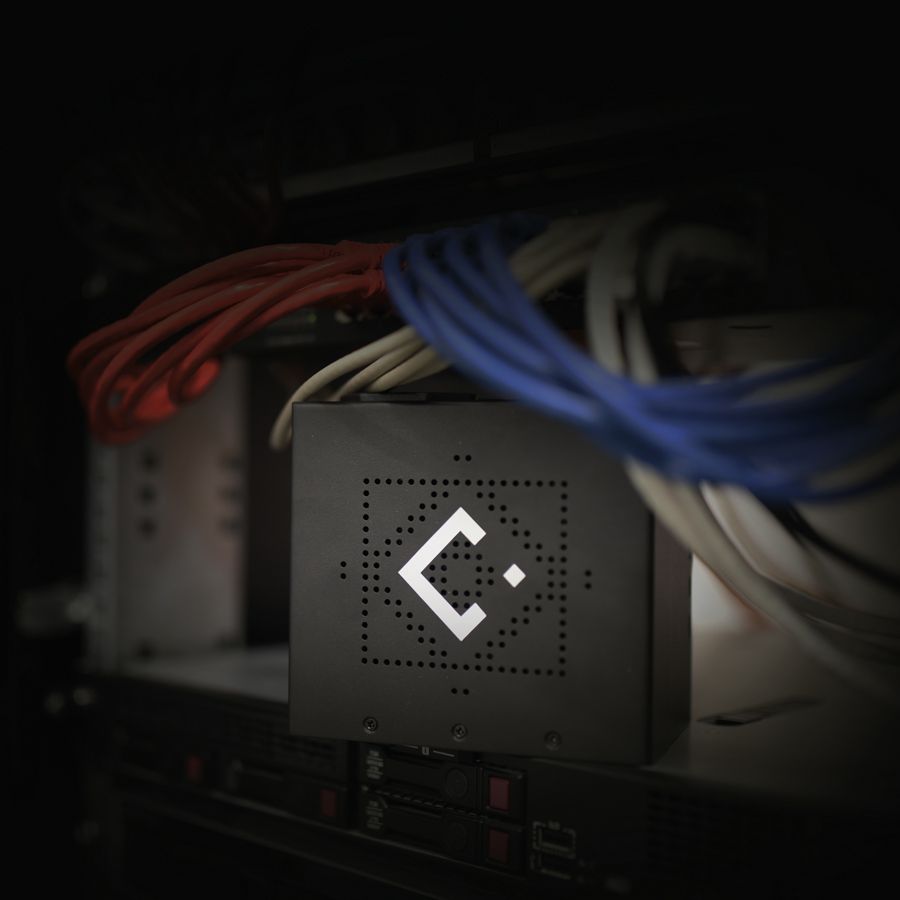
While firewalls and antivirus stop at the perimeter, LECS protects the entire network and all types of devices, whether IT, OT or IoT, thus covering even the most vulnerable areas. No need to configure it: just plug it in and you have an active and continuous defence, day and night.
Every company has different IT security needs depending on its technological infrastructure and the environment in which it operates. Discover our recommended products and devices for each type of business.





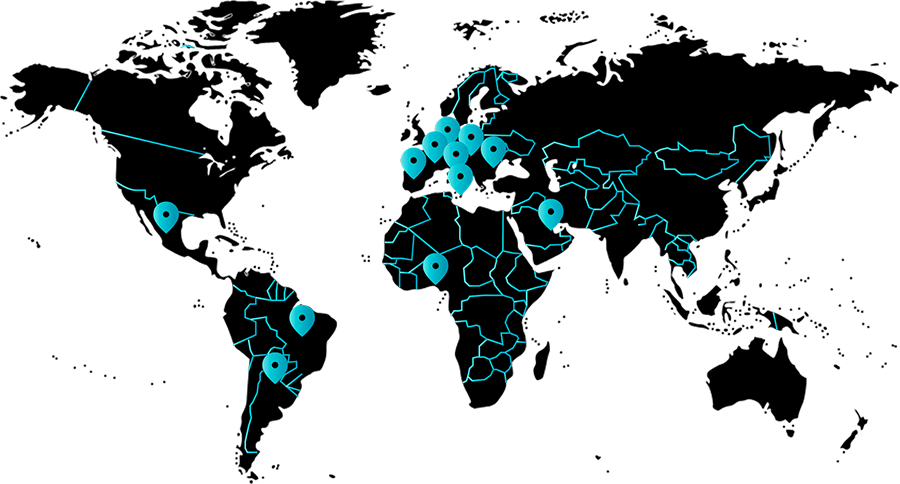
LECS is already at the side of companies all over the world.
Thanks to our patented technology and ease of use, thousands of networks and critical devices in every industry can be protected, ensuring global security without borders.

LECS is a product of Cyber Evolution S.r.l.
Via Erasmo Mari, 57/s
63100 Ascoli Piceno (AP)

The productive investment project-ID 16819-implemented by CYBER EVOLUTION, under the 2014/2020 ROP ERDF Marche – ASSE 8 – INTERVENTION 21.1.1 Call for Proposals “Support for productive investments in order to boost economic growth and competitiveness of areas affected by the earthquake,” supported business growth through productive investments on the real estate and technological structure.

