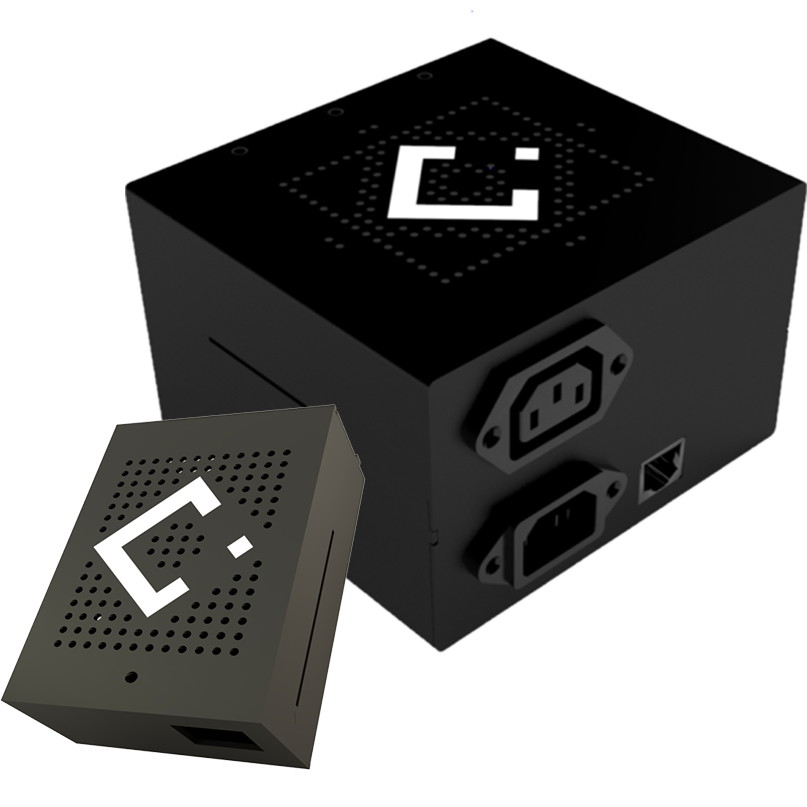
The first Plug&Play cybersecurity blackbox
Protect your infrastructure with LECS, the first Plug & Play cybersecurity device that protects any LAN, Cloud infrastructure and industrial facilities from the most dangerous cyber attacks and threats.
ACTS WHERE THE FIREWALL CANNOT

Zero Knowledge Security Network
LECS has zero knowledge architecture and is maintenance-free. Connected to the network router or switch, the LECS cybersecurity device analyzes traffic, movements inside and outside the network, and once an anomaly is detected, it classifies it and acts according to the degree of severity with a modulated response to the attack.
LECS is the ideal partner for lateral movement detection, ransomware, and data-exfiltration.
MULTILEVEL SECURITY ENGINE
The technology of LECS is based on 3 engines that serve as the cornerstone for the entire ecosystem. Specto, Raises, and Tiresia are the machine learning algorithms that work synergistically and in parallel to protect an entire network segment, performing anomaly detection and classification on network traffic, acting with countermeasures and targeted responses in cases of critical threats, and performing intelligent prediction that provides update feedback based on the latest detected statistics.
How it works
Check & connect LECS
Place LECS at the most strategic point in your infrastructure and connect the device to your network switch. LECS defends your network from internal and external threats while ensuring maximum privacy as it only passively monitors traffic.
TRAP & DETECTION ANALYSIS
LECS acts as a passive strategic network trap. Confused with hosts, it analyzes threats in real time from within the network by classifying them according to the severity of impact.
It also acts as a long-term LOG store by retaining all monitoring statistics.
Impact Isolation Response
In case of high-impact threat, the dual nature disconnection motor intervenes:
Energetic – Physical “L.0” OSI, according to patented procedure.
Procedural – Link L2, 3 OSI, according to patented procedure.
Immediate alert notification sent via email/app.
Inspection & Recovery Network
Following the countermeasure, LECS restores the network connection, checks for additional threats, and through the Tiresia algorithm, learns and parameterizes the threat data in the cloud.
Products and devices for your cybersecurity
Every business has different cybersecurity needs depending on its technology infrastructure and the environment in which it operates. Discover our recommended products and devices for each type of business.

LECS
Version with countermeasure procedural software. Recommended for SMEs, professional firms, web agencies

LECS +
Version with hardware energy countermeasure.
Recommended for Companies, Public Administrations
SaaS
Virtualized version procedural installable on servers, individual clients and Cloud systems.

Industry / corporate
Custom version implementable in Rack. Customizable countermeasures.
