LECS / Technology
THE INTELLIGENT SYSTEM THAT NEVER SLEEPS
A Plug & Play system powered by AI for continuous protection.
LECS brings the most advanced technologies used in critical environments within everyone’s reach.
Blackbox and Air-Gap are just a few examples of procedures used in military and aviation applications.

Today, in many business environments it is difficult to implement complex cyber security solutions and ecosystems especially to manage without specific know-how.
This is why simplifying the approach to cyber security allows companies and professionals to protect their infrastructure.
Our ethical mission therefore encompasses the deployment of scalable security solutions for all.
At the heart of LECS technology are three engines: Specto, Raises and TiresIA.

Specto’s Hidden Analysis Classification Logging (HACL) model is at the heart of fully automated real-time threat detection and management operations. Its stealth approach allows it to remain hidden and work in parallel with the network, without impeding normal operations, all while the advanced algorithm analyses and classifies threats and anomalies on the network in real time.

All operations are supported by the intelligent Tiresia algorithm, which continuously learns and improves not only detection, but also future attack predictions. In fact, it is the first digital intelligence that goes beyond prevention itself, making real cyber threat predictions, thereby greatly increasing the detection capabilities of the entire ecosystem.

If a high-risk criticality is detected, the Raises automatic countermeasure intervenes with a procedural and adaptive response, going through different response steps until the last defence of the patented energy response. This technology ensures the most efficient response against all types of threats and lateral movement.
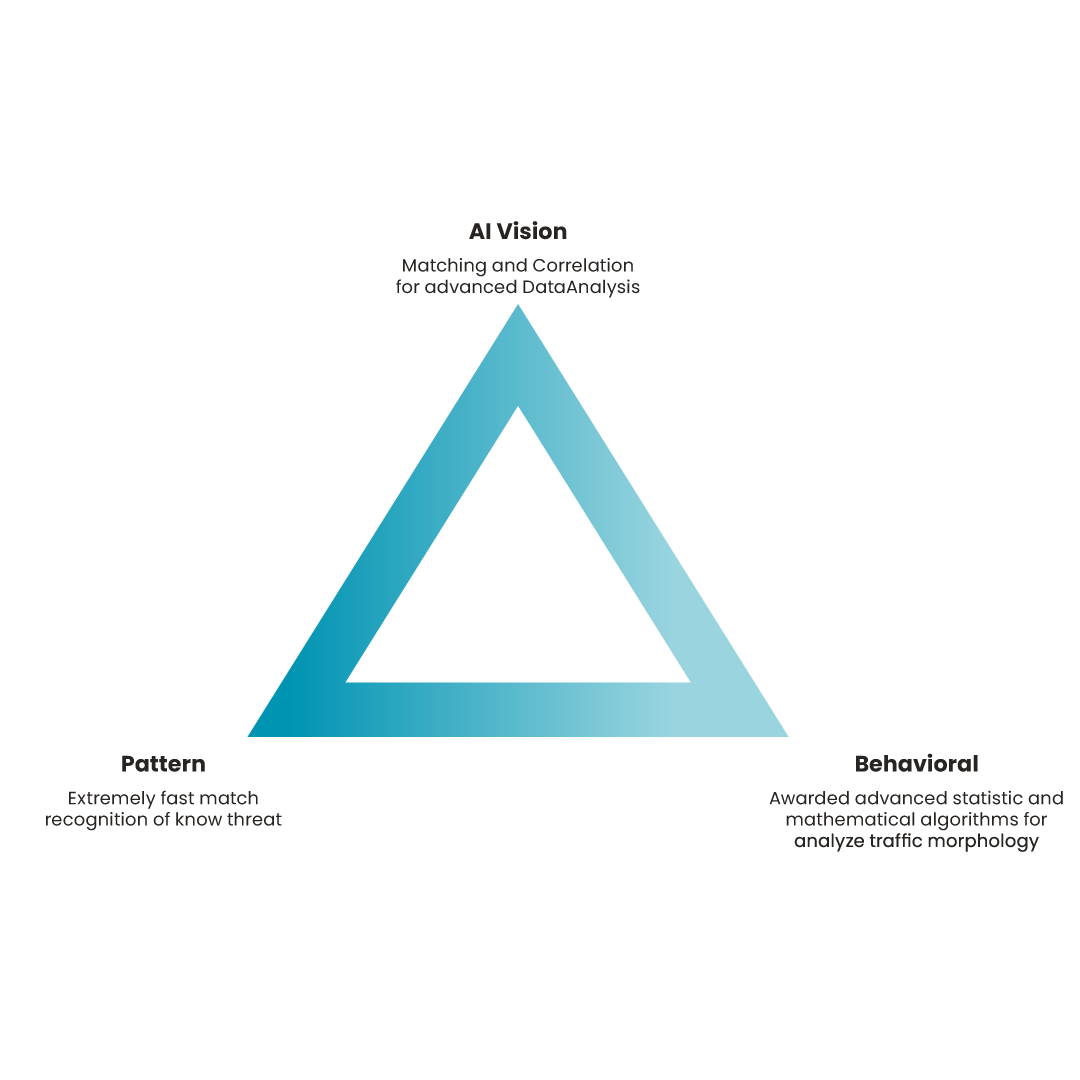
Each corner of the triangle represents an essential component of the detection strategy, designed to address threats from all perspectives:
This unique combination allows LECS to act quickly, accurately and effectively, ensuring that no threat goes unnoticed. The triangle represents the perfect synergy between artificial intelligence, data analysis and predictive capability: a dynamic defence optimised for each environment.
LECS is designed to fit flexibly and efficiently within any IT environment, either through embedded integration directly into devices or by connecting to SIEM systems.
This integration capability allows LECS to enrich the functionality of security systems with its advanced threat detection and response technology

LECS is a product of Cyber Evolution S.r.l.
Via Erasmo Mari, 57/s
63100 Ascoli Piceno (AP)

The productive investment project-ID 16819-implemented by CYBER EVOLUTION, under the 2014/2020 ROP ERDF Marche – ASSE 8 – INTERVENTION 21.1.1 Call for Proposals “Support for productive investments in order to boost economic growth and competitiveness of areas affected by the earthquake,” supported business growth through productive investments on the real estate and technological structure.

